Welcome Back!!
In the last blog we discussed about VRF-Lite introduction & configuration, which is a feature to achieve multi-tenancy (Network isolation) in VMware NSX.
This is part-2 of VRF-Lite series, where we will perform route leak among two different VRF.
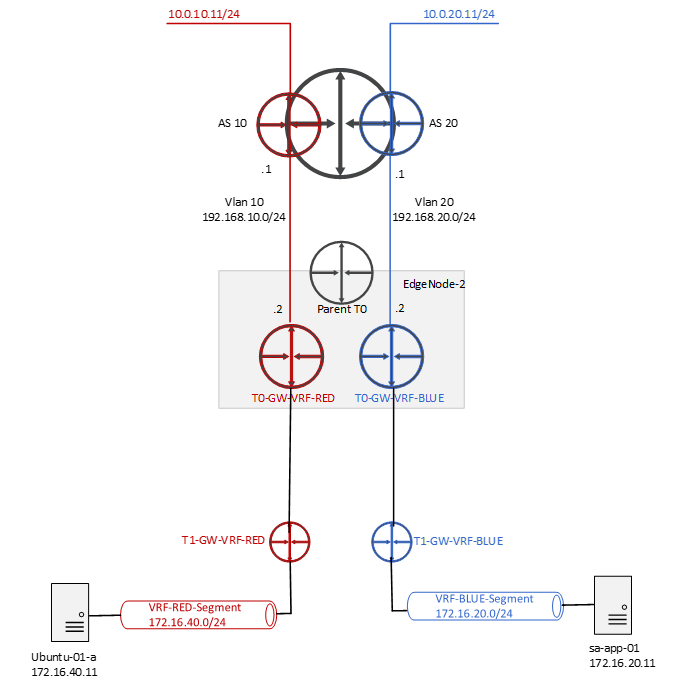
Above is the topology which we are going to discuss in this blog.
- Let’s first validate the routing isolation among both VRF’s.
- Aim is to leak route for the /32 IPs, that is 172.16.40.11 should be able to communicate with 172.16.20.11 & vice versa.


==============================================================================================================
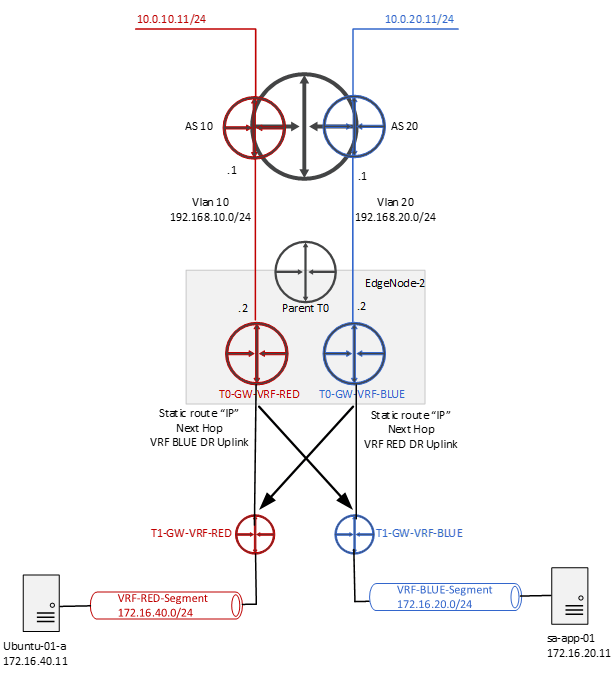
Since we have validated the routing isolation among two VRF instances, lets talk about Route leak among them.
- Route leak is only applicable for multi-tier topology, that is… there must be a Tier-1 connected to Tier-0,
reason being, NSX achieve route-leak via static route on VRF-Tier0 pointing it towards Tier-1 DR uplink. (Refer below diagram)
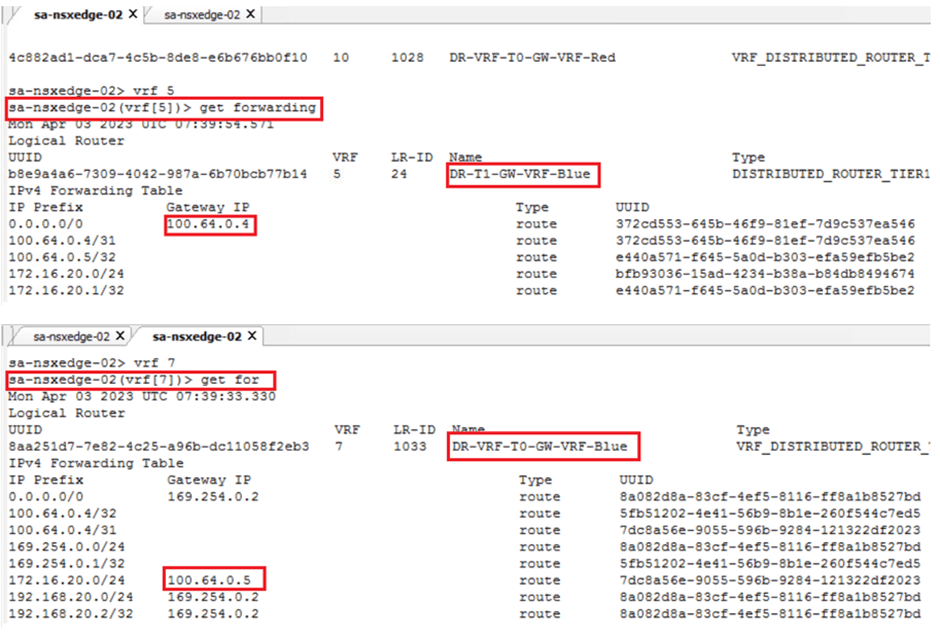
Capture Tier-1 DR IP address for VRF RED
Tier-1 DR IP address can be captured from NSX UI as well as from NSX edge-node CLI.


Capture Tier-1 DR IP address for VRF BLUE

==============================================================================================================
Added captured Tier-1 DR IP in the network topology for easier reference.

==============================================================================================================
Configure Static Route on VRF-RED.
- 172.16.20.11/32 (VRF Blue VM) > Next hop > 100.64.0.5 (DR Uplink VRF-Blue-Tier-1) with scope – VRF Blue
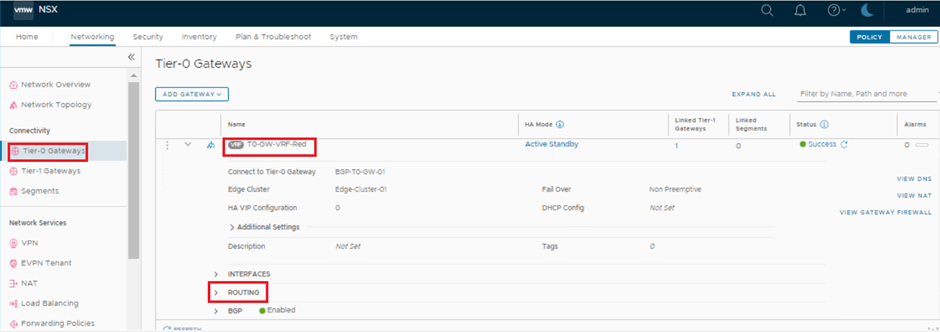




Configure Static Route on VRF-BLUE
- 172.16.40.11/32 (VRF RED VM) > Next hop > 100.64.0.3 (DR Uplink VRF-RED-Tier-1) with scope – VRF RED




==============================================================================================================
Route leak Validation –
- via Ping – Run a ping test cross VRF.


- via Route learning – validate /32 static route learning which we configured above.


This is it for today’s blog, will discuss any new topic/content in our upcoming blogs.
PS: Any Improvement points or suggestions are welcome.
—–Thank You—–
Prashant Pandey


There are now in NSX better methods for veg route exchange in recent version, This old methods lacks any security, newer versions allow separate and independent route control on both sides
LikeLiked by 1 person